Why some VPNs are blocked and others are not

Introduction
More and more people worldwide use VPNs — some for safety on public Wi-Fi, some to bypass regional blocks, others for privacy. VPNs are no longer niche — they are a necessity for millions of everyday users.
There is one important point many miss: not all VPNs are the same. Different services use different technologies, and that directly determines whether you truly get access or your request is detected and blocked. It is crucial to understand which technologies a service uses.
Internet censorship is also a technology. And like VPNs, it evolves. Methods that were effective years ago may now be easy to detect and neutralize. Early protocols like PPTP and L2TP fit the early 2000s, but today even basic filters can block them. They are easy to recognize because they use predictable data patterns.
Then came more advanced options like OpenVPN and WireGuard. They improved reliability and encryption. However, they still have a weak spot: a protocol fingerprint — a distinctive pattern that DPI (Deep Packet Inspection) can use to tell it is not ordinary HTTPS but a VPN. Once such traffic is spotted, it can be blocked or throttled.
Every new wave of blocking triggers new evasion techniques. On one side, ISPs and state filters increasingly use DPI, block ports, check certificates, and analyze traffic behavior. On the other side, VPN developers and enthusiasts create more sophisticated ways to “hide” a VPN connection as ordinary, legitimate traffic.
That is how cutting-edge approaches like Xray-core, VLESS, and Reality appeared. Together they make traffic extremely hard to distinguish from normal web browsing. They do not just encrypt your traffic — they make it indistinguishable from regular HTTPS to most filters.
Let us see how this works and why it is so effective, especially under aggressive censorship.
Unpacking the stack
Foundation: TCP and TLS
Imagine the Internet as a giant postal service. TCP is the reliable courier, and TLS is the sealed envelope. In short: TCP, TLS, encryption — the base of secure delivery.
- TCP — a reliable courier that always delivers “with a signature”.
- TLS — the encryption envelope: even if intercepted, the attacker sees only a sealed letter.
The core idea is to wrap the VPN connection in a familiar envelope so it looks like normal HTTPS. Modern filtering can still detect clumsy disguises, so the camouflage must be careful: imitate real browsers, real patterns. For the provider it should look like an ordinary HTTPS session.
Xray — the “camouflage workshop”
Continuing the postal analogy, Xray is not the courier — it is the packaging and sorting facility by your side that prepares outgoing traffic. What it can do with your parcel:
- Re-pack: change a blatant “VPN envelope” to a normal box resembling a big-store shipment.
- Re-route: hide the inner parcel among others so it looks like a routine delivery.
- Relabel: adjust addressing and metadata to match ordinary HTTPS patterns.
- Alternate paths: send via multiple processing hops so filters do not see recognizable chains.
Xray does not “encrypt the contents” (TLS does that) and is not the courier — it is the instrument that decides how to package and send your parcel without drawing attention. It adapts to the network dynamically, and on Xray the other bypass pieces run — including VLESS and Reality. It is the brain of the system.
VLESS: the lightweight, invisible courier
Our parcel is prepared and sealed with TLS; now it needs a courier. Some couriers look suspicious and get stopped. VLESS is a new-generation courier that stays unobtrusive.
Technically, it avoids distinctive markers; control data is minimal and neutral; it runs inside TLS.
For an ISP, VLESS traffic looks like an ordinary HTTPS site visit — no bright DPI signals.
VLESS is an ideal courier: light, fast, and hard to single out.
Reality: the main bypass technique
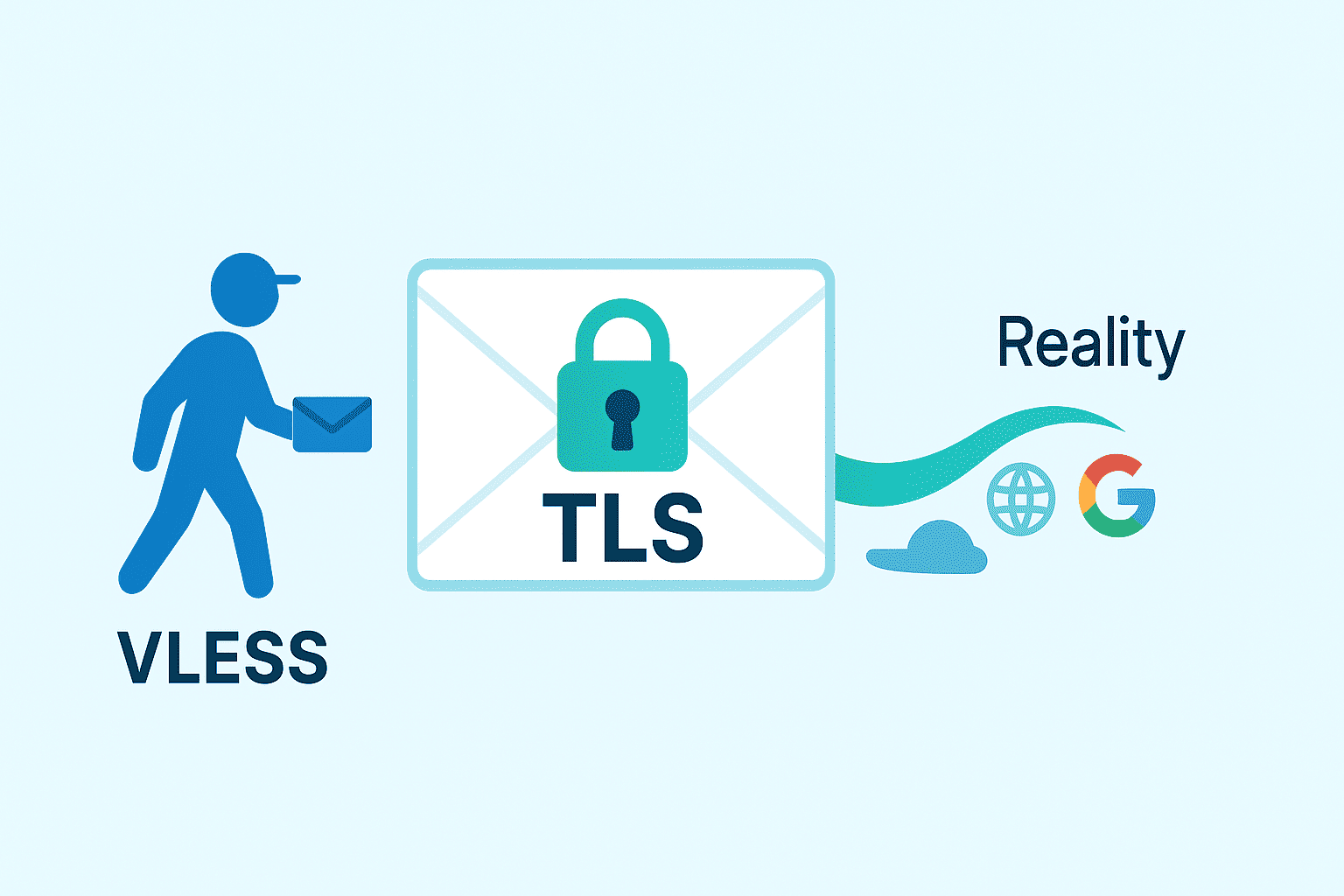
Reality is the “magic” part. In the past, if a courier tried to pass with a fake badge, security could stop them. Even if the letter was sealed (TLS), the courier still looked suspicious.
Reality uses a smarter trick: walk in with the real employees, so nobody notices.
What this means technically
Reality makes your connection look exactly like a visit to a known, trusted site. It uses the same signals as ordinary HTTPS: the same domain in SNI, the same handshake sequence, and real, valid certificates.
A small caveat
Very aggressive filters can employ heavier methods (e.g., blocking IP pools). But in most cases Reality gives filters no reason to interfere — the connection appears normal.
Conclusion
Now the whole picture fits together.
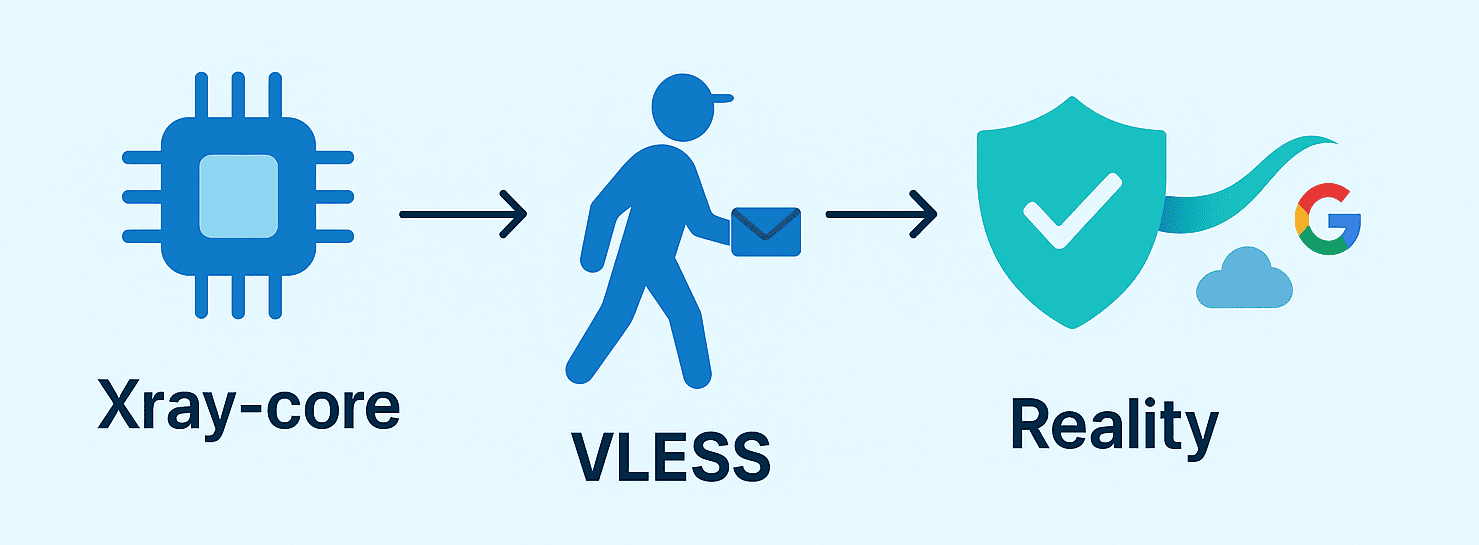
Our solution relies on three modern technologies, each playing a specific role in bypassing blocks — parts of a single robust mechanism.
- Xray-core — the flexible foundation and “brain” of the system. It orchestrates routing, chooses the best path, and adapts to conditions.
- VLESS — the unobtrusive courier that carries traffic without obvious VPN traits. Its sessions look like regular HTTPS, so providers do not flag them.
- Reality — the brilliant camouflage that makes VPN traffic look like a genuine connection to a popular site such as Google or Cloudflare.
Together these technologies form a reliable shield and sword against blocking. Your connection is not merely encrypted — it vanishes from filters’ view, blending into ordinary web traffic.
As long as trusted sites and standards like HTTPS exist, your VPN stays online. Our service uses this advanced stack — Xray-core + VLESS + Reality — so you can stay connected without limits, wherever you are.